Fotolia
AI and edge computing security
While boasting benefits such as reduced latency, edge computing can increase a company's vulnerability. Ensuring security is crucial to getting the most out of the technology.
Edge devices and edge computing have become increasingly popular over the past several years. According to Statista, there are over 22 billion IoT devices connected and billions more phones, computers, and all manner of printers and cameras as of 2018. These devices all sit on the "edge" of the network and are the final point at which computing happens.
Edge computing is considered anything at the edge of a network which could include mobile devices, cameras, IoT devices, smart TVs and even vehicles. Rather than having to send information to a data center, edge computing allows for the information to be processed at or closer to the device thus lowering latency.
Increasingly, AI is being used on these edge devices to increase the sophistication of their capabilities. However, along with the benefits of having AI operate at the edge, some experts are warning of security concerns that could come along with edge computing. Experts are warning that more data security will be needed to counter the new security risks.
How is edge computing related to artificial intelligence?
AI is being integrated into almost every device that we are using. Before long, it will be commonplace for devices such as cellphones, security cameras and other IoT devices to be AI-enabled. Capabilities such as image recognition, natural language processing, pattern and anomaly detection, and all manner of machine learning-enabled abilities could find their way onto these devices.
AI is also being used to manage the devices themselves by reducing their impact on the network and increasing battery life. Data processing with AI will be near instantaneous. Best of all, the introduction of AI on these devices can increase security as files don't have to be sent across a network to be analyzed.
Wearable devices are uniquely better suited to benefit from the use of AI. When these devices are connected, data is much easier to gather, analyze and transmit. With the power of AI on a phone or device one could connect all the wearable technology and detect health issues, anomalies or anything else that might be of concern and require a medical professional.
Edge technology is also helping power autonomous vehicles. AI at the edge allows vehicles to have a network connecting all their sensors and devices on board. The lower latency provided by the edge network allows for real-time information on traffic and the car's surroundings. It also allows for quick communication between autonomous vehicles on the road. For example, your car could get alerts of hazards further down the road and have it offer you suggested reroutes or avoid dangerous situations.
What are the cybersecurity concerns with edge devices?
With the greater use of AI on these edge devices, comes a greater vulnerability. Cybersecurity risks increase with company data being stored and used on the devices on the edge of the network. Everything that interacts with the system becomes another vulnerable point. AI is being used to unlock phones with facial recognition technology and also control access to private data. If these AI systems are compromised, then attached accounts and private information are as well. This can have significant consequences if they are inappropriately accessed or tampered with.
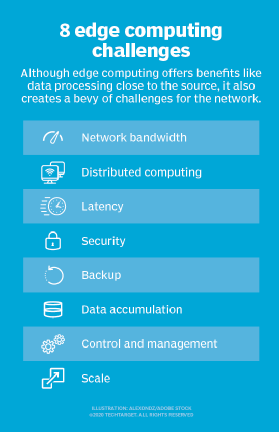
Many off-the-shelf edge devices that connect to networks are not updated as often as they should be. When they are created and there is no built-in security on these devices, they are particularly vulnerable to malware. As a result, criminals have found loopholes in these devices and breaches have occurred. Every device on the local network presents a security risk.
In much the same way that access control systems can be tampered with, so too can the machine learning-models that power edge AI systems. If these models are replaced with models that have loopholes or if criminals can find ways to exploit existing loopholes, then systems that depend on AI capabilities such as surveillance cameras and voice assistants, can become significant security threat vectors. Locking down machine learning models and treating them as a primary asset to be protected will become key to avoiding the next generation of cyberattacks.
Since edge technology is readily available and many devices are relatively inexpensive, it allows for almost anyone to get a hold of the technology and analyze it for vulnerabilities. With access to the technology, creating malicious software is much easier. Because of this, it's far too easy to be left open and vulnerable to attack.
Introducing standards at the edge
AI systems are still relatively nascent, with one of the biggest risks being the lack of standards for secure AI processes and development. When it comes to AI at the edge, these issues are especially common. Standards do more than just create guidelines for businesses to follow. Standards also help to protect the security of the device and network that it is connected to.
The cybersecurity industry will need to craft AI-specific approaches to deal with the new, emerging risks that AI pose, especially in use at the edge. By creating standards, companies would have general guidelines to follow allowing for greater quality and overall consistency.
Like with almost all technology, edge computing and AI-enabled edge devices bring with them a lot of potential. At the same time, they also bring some potential risks. Before implementing edge computing, vulnerabilities need to be identified and addressed and your system must be secured as much as possible in order to prevent malicious attacks.
At the end of the day, these AI-enabled edge devices can bring about cost savings, process improvement and increase the speed of processes and delivery that traditional cloud-based systems can't provide.






